Back in January, I wrote about Anonymization and mentioned PortableTor from a USB stick. The Easter break allowed me to try it on a USB I just got from CD-R King (Php 480 for 4GB ain’t bad). Long story short, Tor was originally made by the US Naval Research Lab and has been said to be used by some three letter US Agencies to shadow people on the net. It works by bouncing your packets around a distributed network of relays run by volunteers all over the world. However, its also been used by some hackers to keep their anonymity even though Wikipedia describes its limitations as:
“Tor cannot (and doesn’t try to) protect against an attacker who can monitor both traffic going into the Tor network and also traffic coming out of the Tor network, such as the United States government which has the capability to monitor any broadband internet traffic under the Communications Assistance For Law Enforcement Act and can therefore see both ends of the Tor connection. Tor tries to protect against traffic analysis, but Tor does not have the ability to prevent traffic confirmation (also called ‘end-to-end correlation’).”
Being in Manila, I wonder what capability the Philippine government has with regard to monitoring broadband traffic. I know they have some, I’m just not sure about the extent.
You can check out the Tor Project site here.
I’ll be re-doing it from scratch for this article and will be giving step by step instructions. I recommend running from a USB for people who frequent Net Cafe’s. For this article I’ll just be using Portable Firefox and not the whole suite available at Portable Apps and will be using an old 512MB drive on L:
Typical caveat: I have no idea if this will work for you and please do back up before you try this.
Step 1
Get Mozilla Firefox Portable then download it to your USB drive (Around 8 MB)

Step 2
Download the PortableTor Application to your USB drive (Around 7.8 MB)
Step 3
Click on the Portable Tor App executable on your USB drive and extract it to your USB drive

Step 4
Do the same for Mozilla Firefox Portable (I had to point to my USB drive letter which in this case is drive L:)
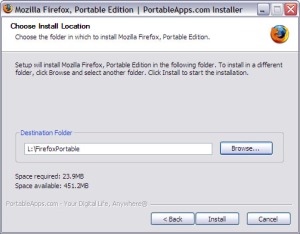
Step 5 (Optional)
Delete the Installer Files (NOT the folders).
Step 6
Go into the PortableTor folder and click on PortableTor.exe
You should then see additional icons on your system tray (typically on the lower right which contains the clock), and if you have a an application firewall (and you should), it will prompt you if you want to allow the applications (yes its plural) access to the Internet

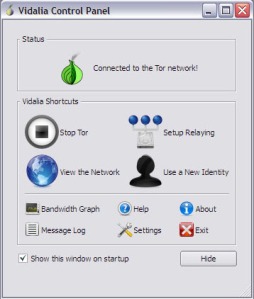
Step 7
Go back to your Firefox Portable folder and click on FirefoxPortable.exe (You are then prompted whether or not to store your session on your USB stick)
Step 8
Once Firefox is running from your USB, go to Tools>Options>Advanced>Network
Then click on Settings and check if you are using local host and port 8118 (You can change this port but I won’t be discussing that here) which is the default port of PortableTor

Tools>Options>Advanced>Network>Settings
Step 9
Head over to What Is My IP Address? to check if it works.

What is My IP Address?
Step 10
You can then check where your assigned IP is by clicking on the number, in this case, Stockholm… yes I’m in Stockholm because I couldn’t stand the summer heat of Manila… NOT.
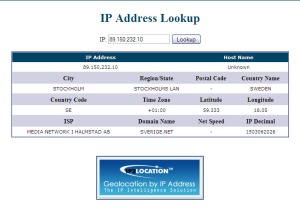
So that’s it, you can run more anonymously on the net using PortableTor, albeit much slower than usual (also dependent upon the particular proxy you’re using). In my limited, unscientific testing, my download speeds varied from 1/5th to 4/5th’s its usual speed. The Tor network also encourages you to run a relay (the bandwidth of which you can limit) so that the overall speed of their network becomes a bit faster.
I haven’t tried this out for Instant Messaging, but I soon will.
If you found the above do it yourself USB for Anonymized Browsing interesting, you might also want to check out the XeroBank Browser which its site says to be, “the most popular free and open-source anonymous web browser in the world, with over 9 million downloads.”
Info Sec News
(BusinessWorld Online) BSP urges tighter e-banking security
(Computerworld Ph) CICT: Timetable for 2010 automated polls tight
(Inquirer.net) COMELEC Chief Says, ‘No more debates on poll automation’
(PhilStar.com) UP Diliman holds first campus-wide automated polls
(IT Matters.com.ph) Online filing system bogs down one day before April deadline
(IT Matters.com.ph) BPO office builders ditch expansion plans
(IT Matters.com.ph) Ayala outsourcing unit bullish of prospects amid downturn
(IT Matters.com.ph) Convergys opening three more contact centers, to hire 3,100
(Reuters) Facebook, YouTube at work make better employees: study
The H Security Conficker Information Site
(The H Security) Conficker test
(The H Security) Simple Conficker test for end users (Description)
(University of Bonn) Conficker Online Infection Indicator
(Computerworld UK) Police e-crime unit teams with banks for first arrest
(SearchSecurity) RSA panel to discuss surveillance, privacy concerns
(Wash Post Security Fix Blog) Report: China, Russia Top Sources of Power Grid Probes
(The Register) Student sentenced for F-ucked up grade hack
(SecurityFocus) Microsoft patches a passel of flaws
(SecurityFocus) Twitter targeted by XSS worms
(SearchSecurity) Oracle issues 43 updates, fixes serious database flaws
(Reuters Video) Symantec sees more malicious threats (approx 2 mins)
(Inquirer.net) Book a bed and breakfast, catch a ‘virus’
(SC Mag US) Despite downturn, IT security spending to increase
(Computerworld) Privacy rules hamper adoption of electronic medical records, study says
(Computerworld) ‘Mafiaboy’ spills the beans at IT360 on underground hackers
(Computerworld) 1 in 5 Windows PCs still hackable by Conficker
(Computerworld) Botnet operators may be able to profit from Conficker update
(Trend Micro News) Trend Micro Discovers New Variant of Conficker: WORM_DOWNAD.E
Site News
Updated the following links pages:
“Software Vulnerabilities” links to “Software Vulnerabilities and Dataloss” and included DatalossDB;
“Security Policy and Best Practices” links to include Information Security Policy World, Windows Security.com’s PDF, Princeton University’s PDF;
“Web App Security” to “Secure Coding and Web App Security” and included US Homeland Security’s Build Security In website